My.comauthorization Services Are Unavailabel Please Try Again in a Few Minutes
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
This commodity helps you resolve single sign-on (SSO) problems with Active Directory Federation Services (AD FS).
Select one of the following section according to the type of consequence that you encounter.
Applies to: Active Directory Federation Services Original KB number: 4034932
NTLM or forms-based hallmark prompt
During troubleshooting unmarried sign-on (SSO) problems with Active Directory Federation Services (AD FS), if users received unexpected NTLM or forms-based authentication prompt, follow the steps in this article to troubleshoot this issue.
Cheque Windows Integrated Hallmark settings
To troubleshoot this issue, check Windows Integrated Authentication settings in the client browser, Advertizement FS settings and hallmark request parameters.
Cheque the customer browser of the user
Check the following settings in Internet Options:
- On the Advanced tab, brand certain that the Enable Integrated Windows Hallmark setting is enabled.
- Following Security > Local intranet > Sites > Advanced, make sure that the Advertizing FS URL is in the list of websites.
- Post-obit Security > Local intranet > Custom level, make sure that the Automated logon merely in Intranet Zone setting is selected.
If you use Firefox, Chrome or Safari, make sure the equivalent settings in these browsers are enabled.
Check the Advertizing FS settings
Check the WindowsIntegratedFallback setting
-
Open Windows PowerShell with the Run every bit administrator option.
-
Get the global authentication policy by running the following control:
Get-ADFSGlobalAuthenticationPolicy -
Examine the value of the WindowsIntegratedFallbackEnbaled attribute.
If the value is True, forms-based hallmark is expected. This means that the authentication request comes from a browser that doesn't back up Windows Integrated Authentication. See the side by side section virtually how to get your browser supported.
If the value is False, Windows Integrated Hallmark should be expected.
Check the WIASupportedUsersAgents setting
-
Get the list of supported user agents by running the following command:
Go-ADFSProperties | Select -ExpandProperty WIASupportedUserAgents -
Examine the listing of user amanuensis strings that the control returns.
Verify if the user agent string of your browser is in the listing. If non, add the user agent string by following the steps beneath:
-
Go to http://useragentstring.com/ that detects and shows you the user agent string of your browser.
-
Get the list of supported user agents by running the following command:
$wiaStrings = Get-ADFSProperties | Select -ExpandProperty WIASupportedUserAgents -
Add together the user agent cord of your browser by running the following control:
$wiaStrings = $wiaStrings+"NewUAString"Example:
$wiaStrings = $wiaStrings+" =~Windows\s*NT.*Border"+"Mozilla/five.0" -
Update the WIASupportedUserAgents setting by running the following command:
Fix-ADFSProperties -WIASupportedUserAgents $wiaStrings
Check the authentication request parameters
Check if the authentication asking specifies forms-based hallmark as the authentication method
- If the authentication request is a WS-Federation request, cheque if the asking includes wauth= urn:oasis:names:tc:SAML:ane.0:am:countersign.
- If the hallmark request is a SAML request, check if the asking includes a samlp:AuthnContextClassRef element with value urn:oasis:names:tc:SAML:2.0:ac:classes:Countersign.
For more information, see Overview of authentication handlers of AD FS sign-in pages.
Bank check if the awarding is Microsoft Online Services for Office 365
If the application that you lot want to access is not Microsoft Online Services, what you experience is expected and controlled by the incoming hallmark request. Work with the awarding possessor to change the behavior.
If the application is Microsoft Online Services, what you experience may exist controlled by the PromptLoginBehavior setting from the trusted realm object. This setting controls whether Azure AD tenants send prompt=login to Ad FS. To set the PromptLoginBehavior setting, follow these steps:
-
Open Windows PowerShell with the "Run as administrator" selection.
-
Become the existing domain federation setting by running the following command:
Become-MSOLDomainFederationSettings -DomainName DomainName | FL * -
Set the PromptLoginBehavior setting by running the following command:
Set-MSOLDomainFederationSettings -DomainName DomainName -PromptLoginBehavior <TranslateToFreshPasswordAuth|NativeSupport|Disabled> -SupportsMFA <$Truthful|$Simulated> -PreferredAuthenticationProtocol <WsFed|SAMLP>The values for the PromptLoginBehavior parameter are:
- TranslateToFreshPasswordAuth: Azure AD sends wauth and wfresh to AD FS instead of prompt=login. This leads to an authentication request to utilise forms-based authentication.
- NativeSupport: The prompt=login parameter is sent as is to Advertising FS.
- Disabled: Nothing is sent to AD FS.
To acquire more almost the Set-MSOLDomainFederationSettings control, see Active Directory Federation Services prompt=login parameter support.
Azure Active Directory (Azure AD) scenario
If the authentication request sent to Azure AD include the prompt=login parameter, disable the prompt=login capability by running the following command:
Set-MsolDomainFederationSettings –DomainName DomainName -PromptLoginBehavior Disabled After you lot run this command, Office 365 applications won't include the prompt=login parameter in each authentication request.
Non Azure AD scenario
Request parameters like WAUTH and RequestedAuthNContext in hallmark requests can have authentication methods specified. Check if other request parameters enforcing the unexpected authentication prompt. If so, modify the request parameter to utilise the expected hallmark method.
Check if SSO is disabled
If SSO is disabled, enable it and test if the issue is resolved.
Multi-factor authentication prompt
To troubleshoot this issue, check if the merits rules in the relying party are correctly set for multi-factor authentication.
Multi-factor hallmark can be enabled at an Advertisement FS server, at a relying party, or specified in an authentication request parameter. Check the configurations to come across if they are correctly set. If multi-cistron authentication is expected only you're repeatedly prompted for information technology, cheque the relying political party issuance rules to run into if multi-gene hallmark claims are passed through to the application.
For more information virtually multi-factor hallmark in AD FS, see the following articles:
- Under the hood bout on Multi-Factor Authentication in ADFS – Part one: Policy
- Under the hood tour on Multi-Factor Authentication in ADFS – Function 2: MFA aware Relying Parties
Bank check the configuration on the AD FS server and the relying party
To check the configuration on the AD FS server, validate the global boosted authentication rules. To bank check the configuration on the relying party, validate the additional hallmark rules for the relying party trust.
-
To check the configuration on the Advertisement FS server, run the following command in a Windows PowerShell window.
Get-ADFSAdditionalAuthenticationRuleTo check the configuration on the relying party, run the following command:
Get-ADFSRelyingPartyTrust -TargetName RelyingParty | Select -ExpandProperty AdditionalAuthenticationRulesNote
If the commands return zero, the boosted authentication rules are non configured. Skip this section.
-
Observe the claim rule fix configured.
Verify if multi-factor hallmark is enabled in the claim rule set
A claim rule set is composed of the following sections:
- The condition statement:
C:[Type=``…,Value=…] - The consequence statement:
=> event (Type=``…,Value=…)
If the effect statement contains the following claim, multi-factor authentication is specified.
Type = "http://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod", Value = "http://schemas.microsoft.com/claims/multipleauthn"
Hither are examples that crave multi-factor authentication to be used for non-workplace joined devices and for extranet access respectively:
-
c:[Type == "http://schemas.microsoft.com/2012/01/devicecontext/claims/isregistereduser", Value == "false"] => outcome(Blazon = "http://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod", Value = "http://schemas.microsoft.com/claims/multipleauthn") -
c:[Type == "http://schemas.microsoft.com/ws/2012/01/insidecorporatenetwork", Value == "faux"] => issue(Blazon = "http://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod", Value = "http://schemas.microsoft.com/claims/multipleauthn")
Check the relying political party issuance rules
If the user repeatedly receives multi-gene authentication prompts after they perform the showtime authentication, it is possible that the replying political party is not passing through the multi-factor hallmark claims to the application. To check if the hallmark claims are passed through, follow these steps:
-
Run the following command in Windows PowerShell:
Go-ADFSRelyingPartyTrust -TargetName ClaimApp -
Notice the rule set defined in the IssuanceAuthorizationRules or IssuanceAuthorizationRulesFile attributes.
The dominion set should include the following issuance rule to pass through the multi-factor hallmark claims:
C:[Type==http://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod, Value==" http://schemas.microsoft.com/claims/multipleauthn"]=>consequence(claim = c)
Check the authentication asking parameter
Cheque if the authentication request specifies multi-gene authentication equally the authentication method
- If the hallmark request is a WS-Federation request, check if the request includes
wauth= http://schemas.microsoft.com/claims/multipleauthn. - If the authentication request is a SAML asking, check if the request includes a samlp:AuthnContextClassRef element with value
http://schemas.microsoft.com/claims/multipleauthn.
For more information, see Overview of hallmark handlers of AD FS sign-in pages.
Check if the application is Microsoft Online Services for Function 365
If the application that you want to access is Microsoft Online Services for Part 365, bank check the SupportsMFA domain federation setting.
-
Get the current SupportsMFA domain federation setting by running the following command:
Get-MSOLDomainFederationSettings -DomainName DomainName | FL * -
If the SupportsMFA setting is Faux, set information technology to True past running the following command:
Ready-MSOLDomainFederationSettings -DomainName DomainName -SupportsMFA $TRUE
Cheque if SSO is disabled
If SSO is disabled, enable information technology and examination if the issue is resolved.
Users can't log in the target site or service
This result tin can occur at the AD FS sign-in page or at the application side.
If the issue occurs at the Advertizement FS sign-in page, you receive an "An error occurred", "HTTP 503 Service is unavailable" or some other error bulletin. The URL of the error page shows the AD FS service name such equally fs.contoso.com.
If the issue occurs at the application side, the URL of the fault page shows the IP address or the site proper name of the target service.
Follow the steps in the following section according where you encounter this effect.
This issue occurs at the AD FS sign-in page
To troubleshoot this upshot, check if all all users are impacted past the issue, and if the users tin access all the relying parties.
All users are impacted past the issue, and the user can't access any of the relying parties
Permit'due south bank check the internal sign-in functionality using IdpInitiatedSignOn. To practise this, utilise the IdpInititatedSignOn page to verify if the AD FS service is upward and running and the hallmark functionality is working correctly. To open up the IdpInitiatedSignOn folio, follow these steps:
-
Enable the IdpInitiatedSignOn folio by running the following command on the AD FS server:
Gear up-AdfsProperties -EnableIdPInitiatedSignonPage $truthful -
From a estimator that is inside your network, visit the post-obit folio:
https://<FederationInstance>/adfs/ls/idpinitiatedsignon.aspx -
Enter the right credentials of a valid user on the sign-in folio.
The sign-in is successful
If the sign-in is successful, check if the Advertisement FS service state is running.
- On the AD FS server, open Server Manager.
- In the Server Manager, click Tools > Services.
- Bank check if the Status of Active Directory Federation Services is Running.
So, check the external sign-in functionality using IdpInitiatedSignOn. Use the IdpInititatedSignOn page to chop-chop verify if the AD FS service is up and running and the authentication functionality is working correctly. To open the IdpInitiatedSignOn page, follow these steps:
-
Enable the IdpInitiatedSignOn page by running the following control on the Advertising FS server:
Gear up-AdfsProperties -EnableIdPInitiatedSignonPage $true -
From a computer that is exterior of your network, visit the following page:
https://<FederationInstance>/adfs/ls/idpinitiatedsignon.aspx -
Enter the correct credentials of a valid user on the sign-in page.
If the sign-in is unsuccessful, see Check the AD FS related components and services and Check the proxy trust human relationship.
If the sign-in is successful, keep the troubleshooting with the steps in All users are impacted past the issue, and the user can access some of the relying parties.
The sign-in is unsuccessful
If the sign-in is unsuccessful, cheque the AD FS related components and services.
Check if the Advert FS service state is running.
- On the Advertizing FS server, open Server Manager.
- In the Server Manager, click Tools > Services.
- Bank check if the Status of Active Directory Federation Services is Running.
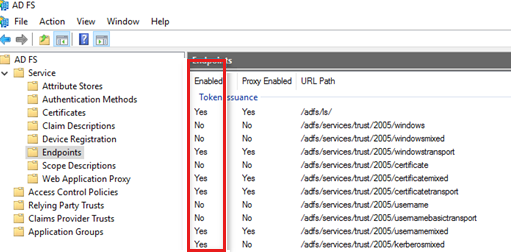
Cheque if the endpoints are enabled. Advertisement FS provides various endpoints for different functionalities and scenarios. Not all endpoints are enabled past default. To check the condition of the endpoints, following these steps:
-
On the Ad FS server, open up the Advertising FS Direction Console.
-
Expand Service > Endpoints.
-
Locate the endpoints and verify if the statuses are enabled on the Enabled column.
Then, check if Azure AD Connect is installed. We recommend that you employ Azure AD Connect which makes SSL certificate direction easier.
If Azure AD Connect is installed, ensure that you use it to manage and update SSL certificates.
If Azure AD Connect is not installed, check if the SSL certificate meets the following AD FS requirements:
-
The document is from a trusted root certification authority.
Advert FS requires that SSL certificates are from a trusted root certification dominance. If Advertising FS is accessed from not-domain joined computers, we recommend that you utilise an SSL certificate from a trusted tertiary-party root certification authority like DigiCert, VeriSign, etc. If the SSL certificate is not from a trusted root certification authorization, SSL advice tin suspension.
-
The subject proper noun of the certificate is valid.
The bailiwick name should match the federation service name, not the AD FS server proper name or some other name. To get the federation service proper noun, run the following control on the principal AD FS server:
Get-AdfsProperties | select hostname -
The certificate is not revoked.
Check for document revocation. If the certificate is revoked, SSL connectedness tin can't be trusted and volition be blocked by clients.
If the SSL document does not run into these requirements, endeavor to get a qualified certificate for SSL advice. We recommend that you use Azure Advertizing Connect which makes SSL certificate management easier. See Update the TLS/SSL document for an Agile Directory Federation Services (AD FS) farm.
If the SSL certificate meets these requirements, bank check the following configurations of the SSL certificate.
Bank check if the SSL certificate is installed properly
The SSL document should be installed to the Personal shop for the local figurer on each federation server in your farm. To install the certificate, double click the .PFX file of the certificate and follow the wizard.
To verify if the certificate is installed to the correct place, follow these steps:
- List the certificates that are in the Personal store for the local computer by running the following control:
dir Cert:\LocalMachine\My - Check if the certificate is in the listing.
Check if the correct SSL certificate is in utilize
Get the thumbprint of the document that is in employ for SSL advice and verify if the thumbprint matches the expected certificate thumbprint.
To get the thumbprint of the document that is in use, run the post-obit command in Windows PowerShell:
Go-AdfsSslCertificate If the wrong certificate is used, set the right document by running the post-obit command:
Set-AdfsSslCertificate –Thumbprint CorrectThumprint Check if the SSL document is set as the service advice certificate
The SSL document needs to exist prepare as the service communication certificate in your Advertising FS farm. This does not happen automatically. To bank check if the correct document is set, follow these steps:
- In the AD FS Management Panel, expand Service > Certificates.
- Verify if the certificate listed under Service communications is the expected certificate.
If the wrong certificate is listed, set the correct certificate, so grant the Advertising FS service the Read permission to the certificate. To do this, follow these steps:
-
Set the right document:
- Right-click Certificates, and and so click Set Service Communication Certificate.
- Select the correct certificate.
-
Verify if the Advertizing FS service has the Read permission to the certificate:
- Add the Certificates snap-in for the local computer account to the Microsoft Management Console (MMC).
- Expand Certificates (Local Figurer) > Personal > Certificates.
- Right-click the SSL certificate, click All Tasks > Manage Individual Keys.
- Verify if adfssrv is listed nether Grouping and user names with the Read permission.
-
If adfssrv is not listed, grant the AD FS service the Read permission to the certificate:
- Click Add, click Locations, click the server, and then click OK.
- Nether Enter the object names to select, enter nt service\adfssrv, click Cheque Names, and and then click OK.
If you lot are using Advertising FS with Device Registration Service (DRS), enter nt service\drs instead. - Grant the Read permission, and then click OK.
Check if Device Registration Service (DRS) is configured in Advertisement FS
If y'all've configured Advertizing FS with DRS, make certain that the SSL document is also properly configured for RDS. For example, if at that place are two UPN suffixes contoso.com and fabrikam.com, the certificate must accept enterpriseregistration.contoso.com and enterpriseregistration.fabrikma.com as the Subject area Alternative Names (SANs).
To check if the SSL certificate has the correct SANs, follow these steps:
-
List all the UPN suffixes being used in the organization by running the following command:
Go-AdfsDeviceRegistratrionUpnSuffix -
Verify if the SSL certificate has the required SANs configured.
-
If SSL certificate does not accept the correct DRS names as SANs, get a new SSL document that has the correct SANs for DRS, so use it every bit the SSL document for AD FS.
Then, cheque the certificate configuration on WAP servers and the fallback bindings:
-
Check if the correct SSL document is set on all WAP servers.
-
Make certain that the SSL certificate is installed in the Personal store for the local computer on each WAP server.
-
Go the SSL certificate used by WAP by running the following command:
Become-WebApplicationProxySslCertificate -
If the SSL certificate is wrong, set up the right SSL certificate by running the post-obit command:
Prepare-WebApplicationProxySslCertificate -Thumbprint Thumbprint
-
-
Check the document bindings and update them if necessary.
To back up non-SNI cases, administrators may specify fallback bindings. Other than the standard federationservicename:443 binding, look for fallback bindings nether the following application IDs:
- {5d89a20c-beab-4389-9447-324788eb944a}: This is the awarding ID for AD FS.
- {f955c070-e044-456c-ac00-e9e4275b3f04}: This is the application ID for Spider web Application Proxy.
For example, if the SSL certificate is specified for a fallback bounden similar 0.0.0.0:443, make sure that the bounden is updated accordingly when the SSL certificate gets updated.
All users are impacted past the event, and the user can access some of the relying parties
First, let's get the relying political party and OAuth customer data. If you utilize a conventional relying party, follow these steps:
-
On the main Advertizement FS server, open Windows PowerShell with the Run equally administrator option.
-
Add together the Advertizement FS two.0 component to Windows PowerShell by running the post-obit control:
Add-PSSnapin Microsoft.Adfs.PowerShell -
Become the relying party data by running the following command:
$rp = Go-AdfsRelyingPartyTrust RPName -
Go the OAuth client information by running the following control:
$customer = Get-AdfsClient ClientName
If you use the Awarding Grouping feature in Windows Server 2016, follow the steps beneath:
-
On the primary AD FS server, open Windows PowerShell with the Run as administrator pick.
-
Get the relying party information past running the following control:
$rp = Get-AdfsWebApiApplication ResourceID -
If the OAuth client is public, get the client information by running the following command:
$client = Get-AdfsNativeClientApplication ClientNameIf the client is confidential, go the client data past running the following command:
$client = Get-AdfsServerApplication ClientName
At present continue with the following troubleshooting methods.
Check the settings of the relying party and customer
The relying political party identifier, client ID and redirect URI should be provided by the owner of the application and the client. However, there could still be a mismatch between what the owner provides and what are configured in Advertizement FS. For example, a mismatch could be caused by a typo. Check if the settings provided by the owner match those configured in AD FS. The steps in the previous page get you lot the settings configured in Advertising FS via PowerShell.
| Settings provided by the owner | Settings configured in Advert FS |
|---|---|
| Relying party ID | $rp.Identifier |
| Relying political party redirect URI | A prefix or wildcard match of
|
| Client ID | $client.ClientId |
| Client redirect URI | A prefix match of $customer.RedirectUri |
If items in the table matches, additionally check if these settings match betwixt what they appear in the authentication asking sent to AD FS and what are configured in Advertising FS. Attempt reproducing the issue during which you capture a Fiddler trace on the authentication request sent past the application to AD FS. Examine the request parameters to practise the following checks depending on the request type.
OAuth requests
An OAuth asking looks like the following:
https://sts.contoso.com/adfs/oauth2/authorize?response_type=code&client_id=ClientID&redirect_uri=https://www.TestApp.com&resource=https://world wide web.TestApp.com
Cheque if the request parameters match the settings configured in AD FS.
| Request parameters | Settings configured in Advertisement FS |
|---|---|
| client_id | $client.ClientId |
| redirect_uri | A prefix match of @client_RedirectUri |
The "resource" parameter should correspond a valid relying party in AD FS. Get the relying party information by running 1 of the following commands.
- If you employ a conventional relying party, run the following control:
Get-AdfsRelyingPartyTrust -Identifier "ValueOfTheResourceParameter" - If you use the Application Group feature in Windows Server 2016, run the following control:
Become-AdfsWebApiApplication "ValueOfTheResourceParameter"
WS-Fed requests
A WS-Fed request looks similar the following:
https://fs.contoso.com/adfs/ls/?wa=wsignin1.0&wtrealm=https://claimsweb.contoso.com&wctx=rm=0&id=passive&ru=/&wct=2014-x-21T22:15:42Z
Check if the asking parameters match the settings configured in AD FS:
| Request parameters | Settings configured in Advertising FS |
|---|---|
| wtrealm | $rp.Identifier |
| wreply | A prefix friction match or wildcard match of $rp.WSFedEndpoint |
SAML requests
A SAML request looks like the following:
https://sts.contoso.com/adfs/ls/?SAMLRequest=EncodedValue&RelayState=cookie:29002348&SigAlg=http://world wide web.w3.org/2000/09/Fxmldsig#rsa-sha1&Signature=Signature
Decode the value of the SAMLRequest parameter by using the "From DeflatedSAML" option in the Fiddler Text Wizard. The decoded value looks like the following:
<samlp:AuthnRequest ID="ID" Version="2.0" IssueInstant="2017-04-28T01:02:22.664Z" Destination="https://TestClaimProvider-Samlp-Only/adfs/ls" Consent="urn:oasis:names:tc:SAML:2.0:consent:unspecified" ForceAuthn="true" xmlns:samlp="urn:haven:names:tc:SAML:2.0:protocol"><Issuer xmlns="urn:oasis:names:tc:SAML:2.0:assertion">http://fs.contoso.com/adfs/services/trust</Issuer><samlp:NameIDPolicy Format="urn:oasis:names:tc:SAML:i.1:nameid-format:unspecified" AllowCreate="true" /></samlp:AuthnRequest> Do the following checks within the decoded value:
- Check if the host proper name in the value of Destination matches the Ad FS host proper name.
- Check if the value of Issuer matches
$rp.Identifier.
Additional notes for SAML:
- $rp.SamlEndpoints: Shows all types of SAML endpoints. The response from AD FS is sent to the corresponding URLs configured in the endpoints. A SAML endpoint tin can utilize redirect, post or artifact bindings for message transmission. All these URLs tin can be configured in AD FS.
- $rp.SignedSamlRequestsRequired: If the value is fix, the SAML request sent from the relying party needs to be signed. The "SigAlg" and "Signature" parameters need to be nowadays in the request.
- $rp.RequestSigningCertificate: This is the signing certificate used to generate the signature on the SAML request. Make sure that the certificate is valid and ask the application owner to match the certificate.
Cheque the encryption certificate
If $rp.EncryptClaims returns Enabled, relying political party encryption is enabled. AD FS uses the encryption certificate to encrypt the claims. Do the following checks:
- $rp.EncryptionCertificate: Utilise this command to get the document and check if it is valid.
- $rp. EncryptionCertificateRevocationCheck: Use this command to check if the certificate meets the revocation check requirements.
The previous two methods don't piece of work
To go on the troubleshooting, see Utilize the Dump Token app.
Not all users are impacted by the outcome, and the user tin can't access any of the relying parties
In this scenario, practice the following checks.
Bank check if the user is disabled
Check the user status in Windows PowerShell or the UI. If the user is disabled, enable the user.
Check the user condition with Windows PowerShell
-
Log in to whatever of the domain controllers.
-
Open Windows PowerShell.
-
Cheque the user condition by running the following command:
Get-ADUser -Identity <samaccountname of the user> | Select Enabled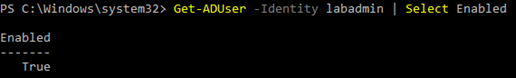
Bank check the user condition in the UI
-
Log in to any of the domain controllers.
-
Open the Agile Directory Users and Computers management console.
-
Click the Users node, correct-click the user in the right pane, then click Properties.
-
Click the Account tab.
-
Under Account options, verify if Account is disabled is checked.
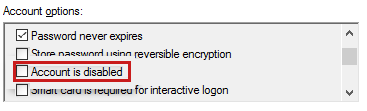
-
If the option is checked, uncheck it.
Bank check if the user properties were updated recently
If any belongings of the user is updated in the Agile Directory, it results in a alter in the metadata of the user object. Check the user metadata object to see which properties were updated recently. If changes are found, make sure that they are picked up by the related services. To bank check if there were belongings changes to a user, following these steps:
-
Log in to a domain controller.
-
Open Windows PowerShell.
-
Get the metadata of the user object by running the post-obit command:
repadmin /showobjmeta <destination DC> "user DN"An example of the command is:
repadmin /showobjmeta localhost "CN=test user,CN=Users,DC=fabidentity,DC=com" -
In the metadata, examine the Time/Engagement cavalcade for each attribute for any clue to a change. In the following case, the userPrincipleName attribute takes a newer date than the other attributes which represents a change to the user object metadata.

Check the forest trust if the user belongs to another woods
In a multi-forest Advert FS environment, a 2-manner woods trust is required between the forest where Advertisement FS is deployed and the other forests which apply the AD FS deployment for authentication. To verify if the trust between the forests is working equally expected, follow these steps:
-
Log in to a domain controller in the forest where AD FS is deployed.
-
Open the Active Directory Domains and Trusts direction console.
-
In the direction console, right-click the domain that contains the trust that you want to verify, then click Properties.
-
Click the Trusts tab.
-
Nether Domains trusted by this domain (outgoing trusts) or Domains that trust this domain (incoming trusts), click the trust to exist verified, and and so click Properties.
-
Click Validate.
In the Active Directory Domain Services dialog box, select either of the options.-
If yous select No, nosotros recommend that you repeat the same process for the reciprocal domain.
-
If you lot select Yes, provide an administrative user credential for the reciprocal domain. There is no need to perform the same process for the reciprocal domain.

-
If these steps did not assist you solve the issue, go along the troubleshooting with the steps in the Not all users are impacted past the result, and the user can access some of the relying parties section.
Non all users are impacted by the issue, and the user can access some of the relying parties
In this scenario, bank check if this upshot occurs in an Azure AD scenario. If so, practise these checks to troubleshoot this issue. If non, see Use the Dump Token app to troubleshoot this issue.
Check if the user is synced to Azure Advertisement
If a user is trying to log in to Azure AD, they volition be redirected to AD FS for authentication for a federated domain. 1 of the possible reasons for a failed login is that the user is not yet synced to Azure AD. You might come across a loop from Azure AD to Advertisement FS later the first authentication attempt at Advertizement FS. To make up one's mind whether the user is synced to Azure AD, follow these steps:
- Download and install the Azure Advertisement PowerShell module for Windows PowerShell.
- Open Windows PowerShell with the "Run every bit administrator" option.
- Initiate a connexion to Azure AD by running the following control:
Connect-MsolService - Provide the global administrator credential for the connection.
- Get the list of users in the Azure AD by running the following command:
Become-MsolUser - Verify if the user is in the list.
If the user is not in the list, sync the user to Azure Advertizement.
Bank check immutableID and UPN in issuance merits dominion
Azure Advertising requires immutableID and the user's UPN to cosign the user.
Note
immutableID is also called sourceAnchor in the following tools:
- Azure AD Sync
- Azure Active Directory Sync (DirSync)
Administrators tin use Azure Advert Connect for automatic management of Ad FS trust with Azure AD. If you are not managing the trust via Azure Advertizement Connect, we recommend that yous do and so by downloading Azure Advertisement Connect Azure Advertising Connect enables automatic claim rules management based on sync settings.
To check if the claim rules for immutableID and UPN in AD FS matches what Azure Advertizement uses, follow these steps:
-
Get sourceAnchor and UPN in Azure Ad Connect.
-
Open Azure Advertising Connect.
-
Click View current configuration.
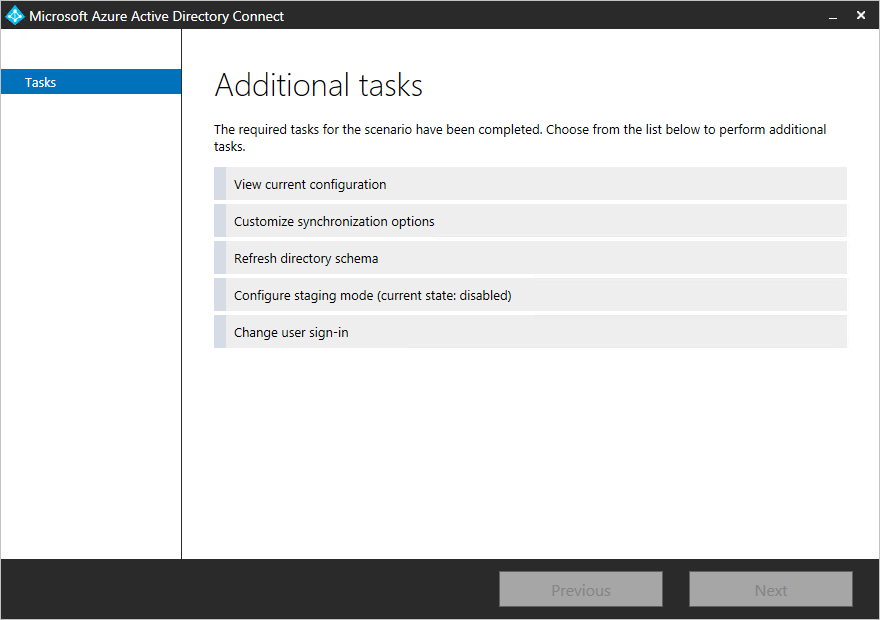
-
On the Review Your Solution page, make a note of the values of SOURCE Anchor and USER Chief Proper name.

-
-
Verify the values of immutableID (sourceAnchor) and UPN in the respective merits rule configured in the Advertizement FS server.
-
On the Advertisement FS server, open the Ad FS management console.
-
Click Relying Party Trusts.
-
Correct-click the relying party trust with Azure AD, then click Edit Claim Issuance Policy.
-
Open the claim rule for immutable ID and UPN.
-
Verify if the variables queried for values of immutableID and UPN are the same as those appear in Azure AD Connect.

-
-
If there is a difference, utilise 1 of the methods beneath:
- If Ad FS is managed by Azure AD Connect, reset the relying party trust past using Azure Ad Connect.
- If AD FS is not managed by Azure AD Connect, right the claims with the correct attributes.
If these checks did not help you solve the issue, see Use the Dump Token app to troubleshoot this issue.
This issue occurs at the application side
If the token signing certificate was renewed recently by AD FS, cheque if the new certificate is picked upward past the federation partner. In instance AD FS uses a token decrypting certificate that was also renewed recently, practise the same check as well. To bank check if the current Advert FS token signing document on Advertising FS matches the i on the federation partner, follow these steps:
-
Get the electric current token signing certificate on AD FS by running the following control:
Get-ADFSCertificate -CertificateType token-signing -
In the list of certificates returned, notice the one with IsPrimary = TRUE, and make a note of the thumbprint.
-
Become the thumbprint of the current token signing certificate on the federation partner. The application owner needs to provide you this.
-
Compare the thumbprints of the two certificates.
Do the same cheque if Advertising FS uses a renewed token decrypting certificate, except that the control to become the token decrypting certificate on Ad FS is as follows:
Become-ADFSCertificate -CertificateType token-decrypting The thumbprints of the two certificates friction match
If the thumbprints match, ensure the partners are using the new AD FS certificates.
If there are certificate mismatches, ensure that the partners are using the new certificates. Certificates are included in the federation metadata published by the Advertizement FS server.
Note
The partners refer to all your resource organisation or account organisation partners, represented in your Advert FS by relying party trusts and claims provider trusts.
-
The partners can access the federation metadata
If the partners tin can access the federation metadata, ask the partners to use the new certificates.
-
The partners can't access the federation metadata
In this case, you must manually ship the partners the public keys of the new certificates. To exercise this, follow these steps:
- Consign the public keys as .cert files, or as .p7b files to include the entire certificate chains.
- Send the public keys to the partners.
- Ask the partners to use the new certificates.
The thumbprints of the two certificates don't match
Then, check if there is a token-signing algorithm mismatch. To exercise this, follow these steps:
-
Make up one's mind the algorithm used by the relying political party past running the following command:
Get-ADFSRelyingPartyTrust -Name RPName | FL SignatureAlgorithmThe possible values are SHA1 or SHA256.
-
Check with the application owner for the algorithm used on the awarding side.
-
Bank check if the two algorithms match.
If the two algorithms friction match, check if the Name ID format matches what the awarding requires.
-
On the Advertising FS server, dump the issuance transform rules by running the following command:
(Get-AdfsRelyingPartyTrust -Name RPName).IssuanceTransformRules -
Locate the rule that issues the NameIdentifier claim. If such a dominion doesn't be, skip this stride.
Here is an instance of the rule:
c:[Blazon == "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"] => issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Value = c.Value, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified");Notice the NameIdentifier format in the following syntax:
Properties["Property-type-URI"] = "ValueURI"The possible formats are listed below. The commencement format is the default.
- urn:haven:names:tc:SAML:1.one:nameid-format:unspecifie.
- urn:haven:names:tc:SAML:1.1:nameid-format:emailAddress
- urn:oasis:names:tc:SAML:2.0:nameid-format:persistent
- urn:oasis:names:tc:SAML:ii.0:nameid-format:transient
-
Ask the awarding owner for the NameIdentifier format required by the application.
-
Verify if the 2 NameIdentifier formats friction match.
-
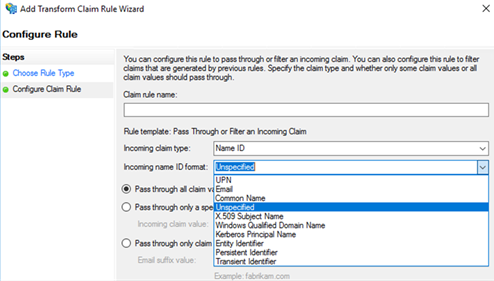
If the formats don't match, configure the NameIdentifier claim to use the format that the application requires. To exercise this, follow these steps:
- Open the AD FS direction console.
- Click Relying Political party Trusts, select the appropriate federation partner, and then click Edit Claims Issuance Policy in the Actions pane.
- Add together a new rule if there is no rule to event the NameIdentifier claim, or update an existing rule. Select Name ID for Incoming claim type, and then specify the format that the application requires.
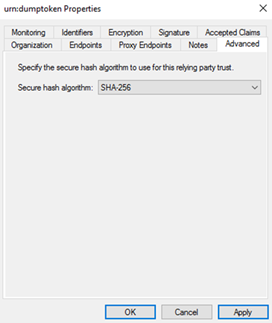
If the 2 algorithms mismatch, update the signing algorithm used by the relying political party trust.
-
Open the AD FS management console.
-
Correct-click the relying political party trust, and then click Properties.
-
On the Advanced tab, select the algorithm to match what the application requires.
Most certificate auto renewal
If the token signing certificate or token decrypting certificate are self-signed, AutoCertificateRollover is enabled past default on these certificates and AD FS manages the car renewal of the certificates when they are close to expiration.
To decide if you're using self-signed certificates, follow these steps:
-
Run the following command:
Get-ADFSCerticate -CertificateType "token-signing"
-
Examine the certificate attributes.
If the Discipline and Issuer attributes both start with "CN=ADFS Signing...", the certificate is self-signed and managed by AutoCertRollover.
To ostend if the certificates renew automatically, follow these steps:
-
Run the following command:
Become-ADFSProperties | FL AutoCertificateRollover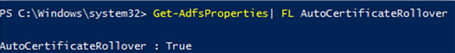
-
Examine the AutoCertificateRollover aspect.
- If AutoCertificateRollover = TRUE, AD FS automatically generates new certificates (30 days prior to expiration by default) and sets them every bit the primary certificates (25 days prior to expiration).
- If AutoCertificateRollover = Imitation, you lot need to manually replace the certificates.
This article introduces how to check the ADFS-related components and services. These steps could help when you are troubleshooting sign-on (SSO) issues with Active Directory Federation Services (ADFS).
Check DNS
Accessing ADFS should point directly to i of the WAP (Web Application Proxy) servers or the load balancer in front of the WAP servers. Practise the post-obit checks:
- Ping the federation service proper noun (e.g.
fs.contoso.com). Confirm if the IP address the Ping resolves to is of 1 of the WAP servers or of the load balancer of the WAP servers. - Check if there is an A tape for the federation service in the DNS server. The A record should point to one of the WAP servers or to the load balancer of the WAP servers.
If WAP is not implemented in your scenario for external admission, check if accessing ADFS points directly to one of the ADFS servers or the load balancer in front of the ADFS servers:
- Ping the federation service name (e.chiliad.
fs.contoso.com). Confirm if the IP address that you get resolves to 1 of the ADFS servers or the load balancer of the ADFS servers. - Cheque if at that place is an A record for the federation service in the DNS server. The A record should bespeak to i of the ADFS servers or to the load balancer of the ADFS servers.
Cheque the load balancer if it is used
Check if firewall is blocking traffic betwixt:
- The ADFS server and the load balancer.
- The WAP (Web Application Proxy) server and the load balancer if WAP is used.
If probe is enabled on the load balancer, check the following:
- If you are running Windows Server 2012 R2, ensure that the August 2014 update rollup is installed.
- Check if port eighty is enabled in the firewall on the WAP servers and ADFS servers.
- Ensure that probe is set for port lxxx and for the endpoint /adfs/probe.
Bank check the firewall settings
Check if inbound traffic through TCP port 443 is enabled on:
- the firewall between the Spider web Application Proxy server and the federation server farm.
- the firewall between the clients and the Web Application Proxy server.
Check if entering traffic through TCP port 49443 is enabled on the firewall between the clients and the Spider web Application Proxy server when the following weather are true:
- TLS client authentication using X.509 certificate is enabled.
- Y'all are using ADFS on Windows Server 2012 R2.
Note
The configuration is not required on the firewall between the Web Awarding Proxy server and the federation servers.
Check if the endpoint is enabled on the proxy
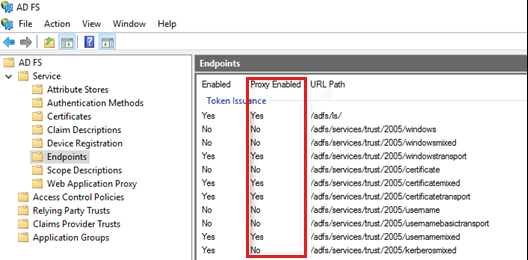
ADFS provides diverse endpoints for different functionalities and scenarios. Not all endpoints are enabled by default. To cheque the whether the endpoint is enabled on the proxy, following these steps:
-
On the ADFS server, open the ADFS Direction Console.
-
Expand Service > Endpoints.
-
Locate the endpoint and verify if the status is enabled on the Proxy Enabled column.
Cheque the proxy trust relationship
If Web Application Proxy (WAP) is deployed, the proxy trust relationship must be established between the WAP server and the AD FS server. Check if the proxy trust relationship is established or starts to fail at some bespeak in time.
Notation
Information on this page applies to Advert FS 2012 R2 and subsequently.
Groundwork data
The proxy trust relationship is client certificate based. When you lot run the Web Application Proxy post-install wizard, the magician generates a self-signed client certificate using the credentials that you specified in the wizard. Then the wizard inserts the document into the AD FS configuration database and adds it to the AdfsTrustedDevices certificate store on the AD FS server.
For any SSL communication, http.sys uses the following priority order for SSL document bindings to match a certificate:
| Priority | Name | Parameters | Description |
|---|---|---|---|
| 1 | IP | IP:port | Exact IP and Port match |
| 2 | SNI | Hostname:port | Exact hostname friction match (connection must specify SNI) |
| iii | CCS | Port | Invoke Key Certificate Shop |
| four | IPv6 wildcard | Port | IPv6 wildcard match (connexion must be IPv6) |
| 5 | IP wildcard | Port | IP wildcard lucifer (connection tin be IPv4 or IPv6) |
AD FS 2012 R2 and afterward are contained of Internet Data Services (IIS) and runs every bit a service on summit of http.sys. hostname:port SSL document bindings are used by Advertising FS. During customer certificate authentication, Ad FS sends a certificate trust list (CTL) based on the certificates in the AdfsTrustedDevices shop. If an SSL certificate binding for your AD FS server uses IP:port or the CTL store is not AdfsTrustedDevices, proxy trust relationship may non be established.
Get the SSL certificate bindings for AD FS
On the AD FS server, run the following control in Windows PowerShell:
netsh http show sslcert
In the list of bindings returned, look for those with the Application ID of 5d89a20c-beab-4389-9447-324788eb944a. Here is an example of a healthy bounden. Note the "Ctl Shop Name" line.
Hostname:port : adfs.contoso.com:443 Certificate Hash : 3638de9b03a488341dfe32fc3ae5c480ee687793 Awarding ID : {5d89a20c-beab-4389-9447-324788eb944a} Certificate Store Name : MY Verify Client Certificate Revocation : Enabled Verify Revocation Using Buried Customer Certificate Merely : Disabled Usage Cheque : Enabled Revocation Freshness Time : 0 URL Retrieval Timeout : 0 Ctl Identifier : (cypher) Ctl Store Name : AdfsTrustedDevices DS Mapper Usage : Disabled Negotiate Client Certificate : Disabled Run script to automatically detect issues
To automatically detect problems with the proxy trust relationship, run the following script. Based on the trouble detected, accept the activity appropriately.
param ( [switch]$syncproxytrustcerts ) office checkhttpsyscertbindings() { Write-Host; Write-Host("1 – Checking http.sys document bindings for potential bug") $httpsslcertoutput = netsh http show sslcert $adfsservicefqdn = (Get-AdfsProperties).HostName $i = 1 $certbindingissuedetected = $false While($i -lt $httpsslcertoutput.count) { $ipport = $fake $hostnameport = $false if ( ( $httpsslcertoutput[$i] -match "IP:port" ) ) { $ipport = $true } elseif ( ( $httpsslcertoutput[$i] -lucifer "Hostname:port" ) ) { $hostnameport = $true } ## Check for IP specific certificate bindings if ( ( $ipport -eq $truthful ) ) { $httpsslcertoutput[$i] $ipbindingparsed = $httpsslcertoutput[$i].split(":") if ( ( $ipbindingparsed[2].trim() -ne "0.0.0.0" ) -and ( $ipbindingparsed[3].trim() -eq "443") ) { $alarm = "There is an IP specific bounden on IP " + $ipbindingparsed[two].trim() + " which may conflict with the Advertisement FS port 443 cert binding." | Write-Alarm $certbindingissuedetected = $true } $i = $i + xiv continue } ## check that CTL Store is set for ADFS service binding elseif ( $hostnameport -eq $true ) { $httpsslcertoutput[$i] $ipbindingparsed = $httpsslcertoutput[$i].split(":") If ( ( $ipbindingparsed[2].trim() -eq $adfsservicefqdn ) -and ( $ipbindingparsed[3].trim() -eq "443") -and ( $httpsslcertoutput[$i+10].split(":")[1].trim() -ne "AdfsTrustedDevices" ) ) { Write-Warning "ADFS Service bounden does not take CTL Shop Proper noun prepare to AdfsTrustedDevices" $certbindingissuedetected = $true } $i = $i + fourteen continue } $i++ } If ( $certbindingissuedetected -eq $false ) { Write-Host "Bank check Passed: No certificate binding issues detected" } } role checkadfstrusteddevicesstore() { ## cheque for CA issued (non-self signed) certs in the AdfsTrustedDevices cert shop Write-Host; Write-Host "ii – Checking AdfsTrustedDevices cert store for not-self signed certificates" $certlist = Become-Childitem cert:\LocalMachine\AdfsTrustedDevices -recurse | Where-Object {$_.Issuer -ne $_.Subject} If ( $certlist.count -gt 0 ) { Write-Warning "The post-obit non-cocky signed certificates are nowadays in the AdfsTrustedDevices store and should be removed" $certlist | Format-List Subject } Else { Write-Host "Check Passed: No non-self signed certs present in AdfsTrustedDevices cert store" } } function checkproxytrustcerts { Param ([bool]$repair=$faux) Write-Host; Write-Host("iii – Checking AdfsTrustedDevices cert shop is in sync with ADFS Proxy Trust config") $doc = new-object Xml $doc.Load("$env:windir\ADFS\Microsoft.IdentityServer.Servicehost.exe.config") $connString = $dr..configuration.'microsoft.identityServer.service'.policystore.connectionString $command = "Select ServiceSettingsData from [IdentityServerPolicy].[ServiceSettings]" $cli = new-object System.Data.SqlClient.SqlConnection $cli.ConnectionString = $connString $cmd = new-object System.Data.SqlClient.SqlCommand $cmd.CommandText = $command $cmd.Connectedness = $cli $cli.Open() $configString = $cmd.ExecuteScalar() $configXml = new-object XML $configXml.LoadXml($configString) $rawCerts = $configXml.ServiceSettingsData.SecurityTokenService.ProxyTrustConfiguration._subjectNameIndex.KeyValueOfstringArrayOfX509Certificate29zVOn6VQ.Value.X509Certificate2 #$ctl = dir cert:\LocalMachine\ADFSTrustedDevices $store = new-object System.Security.Cryptography.X509Certificates.X509Store("ADFSTrustedDevices","LocalMachine") $store.open up("MaxAllowed") $atLeastOneMismatch = $false $badCerts = @() foreach($rawCert in $rawCerts) { $rawCertBytes = [System.Convert]::FromBase64String($rawCert.RawData.'#text') $cert=New-Object System.Security.Cryptography.X509Certificates.X509Certificate2(,$rawCertBytes) $now = Get-Engagement if ( ($cert.NotBefore -lt $now) -and ($cert.NotAfter -gt $now)) { $certThumbprint = $cert.Thumbprint $certSubject = $cert.Subject field $ctlMatch = dir cert:\localmachine\ADFSTrustedDevices\$certThumbprint -ErrorAction SilentlyContinue if ($ctlMatch -eq $null) { $atLeastOneMismatch = $true Write-Warning "This cert is NOT in the CTL: $certThumbprint – $certSubject" if ($repair -eq $truthful) { write-Alarm "Attempting to repair" $shop.Add($cert) Write-Warning "Repair successful" } else { Write-Warning ("Please install KB.2964735 or re-run script with -syncproxytrustcerts switch to add missing Proxy Trust certs to AdfsTrustedDevices cert store") } } } } $store.Shut() if ($atLeastOneMismatch -eq $faux) { Write-Host("Check Passed: No mismatched certs found. CTL is in sync with DB content") } } checkhttpsyscertbindings checkadfstrusteddevicesstore checkproxytrustcerts($syncproxytrustcerts) Write-Host; Write-Host("All checks completed.") Problem 1: At that place is an IP specific binding
The bounden may conflict with the AD FS certificate binding on port 443.
The IP:port binding takes the highest precedence. If an IP:port binding is in the Advertizing FS SSL certificate bindings, http.sys e'er uses the document for the bounden for SSL communication. To solve this problem, use the post-obit methods.
-
Remove the IP:port binding
Be aware that the IP:port binding may come back after you removed it. For case, an application configured with this IP:port binding may automatically recreate it on the side by side service beginning-up.
-
Use another IP accost for Advertisement FS SSL communication
If the IP:port binding is required, resolve the ADFS service FQDN to another IP address that is not used in any bindings. That way, http.sys will apply the Hostname:port binding for SSL advice.
-
Set AdfsTrustedDevices as the CTL Shop for the IP:port binding
This is the terminal resort if you lot can't use the methods above. Simply it is better to empathise the following weather before y'all change the default CTL shop to AdfsTrustedDevices:
- Why the IP:port bounden is at that place.
- If the bounden relies on the default CTL store for client document authentication.
Trouble 2: The AD FS document binding doesn't have CTL Store Proper name set to AdfsTrustedDevices
If Azure AD Connect is installed, use AAD Connect to set CTL Store Name to AdfsTrustedDevices for the SSL certificate bindings on all Advertising FS servers. If Azure Advert Connect is not installed, regenerate the Ad FS document bindings by running the following command on all AD FS servers.
Fix-AdfsSslCertificate -Thumbprint Thumbprint Problem 3: A certificate that is not cocky-signed exists in the AdfsTrustedDevices certificate store
If a CA issued certificate is in a document store where only self-signed certificates would normally exist, the CTL generated from the store would simply contain the CA issued certificate. The AdfsTrustedDevices document store is such a store that is supposed to take just cocky-signed certificates. These certificates are:
- MS-System-Access: The self-signed document used for issuing workplace join certificates.
- ADFS Proxy Trust: The certificates for each Spider web Application Proxy server.
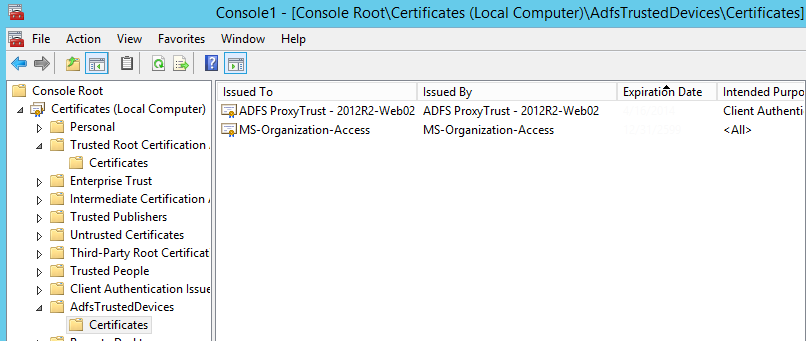
Therefore, delete whatsoever CA issued document from the AdfsTrustedDevices document shop.
Trouble iv: Install KB2964735 or re-run the script with -syncproxytrustcerts
When a proxy trust relationship is established with an AD FS server, the client document is written to the AD FS configuration database and added to the AdfsTrustedDevices certificate store on the AD FS server. For an Advertising FS farm deployment, the customer certificate is expected to exist synced to the other AD FS servers. If the sync doesn't happen for some reason, a proxy trust relationship volition only work against the AD FS server the trust was established with, simply not against the other AD FS servers.
To solve this problem, use ane of the following methods.
Method 1
Install the update documented in KB 2964735 on all Advertizing FS servers. After the update is installed, a sync of the client document is expected to happen automatically.
Method 2
Run the script with the – syncproxytrustcerts switch to manually sync the client certificates from the AD FS configuration database to the AdfsTrustedDevices document store. The script should be run on all the AD FS servers in the farm.
Note
This is not a permanent solution because the client certificates volition exist renewed on a regular basis.
Problem 5: All checks are passed. But the trouble persists
Check if there is a time or time zone mismatch. If time matches but the time zone doesn't, proxy trust relationship will as well fail to be established.
Check if there is SSL termination between the Advertising FS server and the WAP server
If SSL termination is happening on a network device between Advertizement FS servers and the WAP server, advice betwixt AD FS and WAP will pause because the communication is based on client certificate.
Disable SSL termination on the network device betwixt the AD FS and WAP servers.
Utilize the Dump Token app
The Dump Token app is helpful when debugging problems with your federation service equally well as validating custom merits rules. It is non an official solution just a good contained debugging solution that is recommended for the troubleshooting purposes.
Before using the Dump Token app
Before using the Dump Token app, you lot need to:
- Get the information of the relying party for the application you desire to admission. If OAuth hallmark is implemented, become the OAuth customer information as well.
- Ready up the Dump Token app.
Get the relying political party and OAuth client information
If you use a conventional relying political party, follow these steps:
-
On the Advert FS server, open Windows PowerShell with the Run as administrator option.
-
Add together the AD FS 2.0 component to Windows PowerShell by running the following command:
Add-PSSnapin Microsoft.Adfs.PowerShell -
Get the relying party data past running the post-obit command:
$rp = Get-AdfsRelyingPartyTrust RPName -
Get the OAuth client information past running the following command:
$client = Go-AdfsClient ClientName
If you lot use the Awarding Grouping feature in Windows Server 2016, follow the steps below:
-
On the AD FS server, open Windows PowerShell with the Run as administrator option.
-
Get the relying party data by running the following control:
$rp = Get-AdfsWebApiApplication ResourceID -
If the OAuth customer is public, get the client data by running the following control:
$customer = Get-AdfsNativeClientApplication ClientNameIf the OAuth client is confidential, get the customer information by running the following command:
$customer = Get-AdfsServerApplication ClientName
Set upward the Dump Token app
To set up the Dump Token app, run the following commands in the Windows PowerShell window:
$authzRules = "=>result(Type = `"http://schemas.microsoft.com/authorization/claims/let`", Value = `"true`");" $issuanceRules = "ten:[]=>issue(claim=x);" $redirectUrl = "https://dumptoken.azurewebsites.net/default.aspx" $samlEndpoint = New-AdfsSamlEndpoint -Binding POST -Protocol SAMLAssertionConsumer -Uri $redirectUrl Add-ADFSRelyingPartyTrust -Name "urn:dumptoken" -Identifier "urn:dumptoken" -IssuanceAuthorizationRules $authzRules -IssuanceTransformRules $issuanceRules -WSFedEndpoint $redirectUrl -SamlEndpoint $samlEndpoint Now keep with the post-obit troubleshooting methods. At the end of each method, run across if the problem is solved. If not, use another method.
Troubleshooting methods
Cheque the authorization policy to see if the user is impacted
In this method, you start by getting the policy details, and then utilize the Dump Token app to diagnose the policy to meet if the user is impacted.
Get the policy details
$rp.IssuanceAuthorizationRules shows the authorization rules of the relying party.
In Windows Server 2016 and later versions, you tin apply $rp. AccessControlPolicyName to configure authentication and say-so policy. If $rp. AccessControlPolicyName has value, an access command policy is in place which governs the dominance policy. In that case, $rp.IssuanceAuthorizationRules is empty. Use $rp.ResultantPolicy to detect out details about the access command policy.
If $rp.ResultantPolicy doesn't have the details almost the policy, look into the actual claim rules. To get the claim rules, follow these steps:
- Set the admission control policy to $cypher by running the following control:
Set-AdfsRelyingPartyTrust -TargetRelyingParty $rp -AccessControlPolicyName $null - Go the relying party data by running the following command:
$rp = Get-AdfsRelyingPartyTrust RPName - Check
$rp.IssuanceAuthorizationRulesand$rp. AdditionalAuthenticationRules.
Use the Dump Token app to diagnose the say-so policy
-
Gear up the Dump Token authentication policy to be the same as the failing relying party.
-
Have the user open up one of the following links depending on the hallmark policy y'all set.
- WS-Fed:
https://FerderationInstance/adfs/ls?wa=wsignin1.0&wtrealm=urn:dumptoken - SAML-P:
https://FerderationInstance/adfs/ls/IdpInitiatedSignOn?LoginToRP=urn:dumptoken - Force multi-factor authentication:
https://FerderationInstance/adfs/ls?wa=wsignin1.0&wtrealm=urn:dumptoken&wauth=http://schemas.microsoft.com/claims/multipleauthn
- WS-Fed:
-
Log in on the Sign-In page.
What you become is the set of claims of the user. See if there is anything in the say-so policy that explicitly denies or allows the user based on these claims.
Check if any missing or unexpected claim causes access deny to the resource
-
Configure the claim rules in the Dump Token app to exist the aforementioned as the claim rules of the failing relying party.
-
Configure the Dump Token authentication policy to be the same as the failing relying party.
-
Have the user open one of the post-obit links depending on the hallmark policy you set up.
- WS-Fed:
https://FerderationInstance/adfs/ls?wa=wsignin1.0&wtrealm=urn:dumptoken - SAML-P:
https://FerderationInstance/adfs/ls/IdpInitiatedSignOn?LoginToRP=urn:dumptoken - Force multi-factor authentication:
https://FerderationInstance/adfs/ls?wa=wsignin1.0&wtrealm=urn:dumptoken&wauth=http://schemas.microsoft.com/claims/multipleauthn
- WS-Fed:
-
Log in on the Sign-In page.
This is the set of claims the relying party is going to get for the user. If any claims are missing or unexpected, await at the issuance policy to find out the reason.
If all the claims are nowadays, cheque with the application owner to encounter which claim is missing or unexpected.
Check if a device state is required
If the dominance rules check for device claims, verify if any of these device claims are missing in the list of claims you go from the Dump Token app. The missing claims could block device authentication. To go the claims from the Dump Token app, follow the steps in the Use the Dump Token app to diagnose the authorization policy section in the Bank check authorisation policy if the user was impacted method.
The following are the device claims. The authorization rules may use some of them.
-
http://schemas.microsoft.com/2012/01/devicecontext/claims/registrationid -
http://schemas.microsoft.com/2012/01/devicecontext/claims/displayname -
http://schemas.microsoft.com/2012/01/devicecontext/claims/identifier -
http://schemas.microsoft.com/2012/01/devicecontext/claims/ostype -
http://schemas.microsoft.com/2012/01/devicecontext/claims/osversion -
http://schemas.microsoft.com/2012/01/devicecontext/claims/ismanaged -
http://schemas.microsoft.com/2012/01/devicecontext/claims/isregistereduser -
http://schemas.microsoft.com/2014/02/devicecontext/claims/isknown -
http://schemas.microsoft.com/2014/02/deviceusagetime -
http://schemas.microsoft.com/2014/09/devicecontext/claims/iscompliant -
http://schemas.microsoft.com/2014/09/devicecontext/claims/trusttype
If in that location is a missing claim, follow the steps in Configure On-Premises Conditional Access using registered devices to make sure the environment is setup for device authentication.
If all the claims are present, see if the values of the claims from the Dump Token app match the values required in the potency policy.
Source: https://docs.microsoft.com/en-us/troubleshoot/windows-server/identity/troubleshoot-ad-fs-sso-issue
0 Response to "My.comauthorization Services Are Unavailabel Please Try Again in a Few Minutes"
Post a Comment